Software and Performance
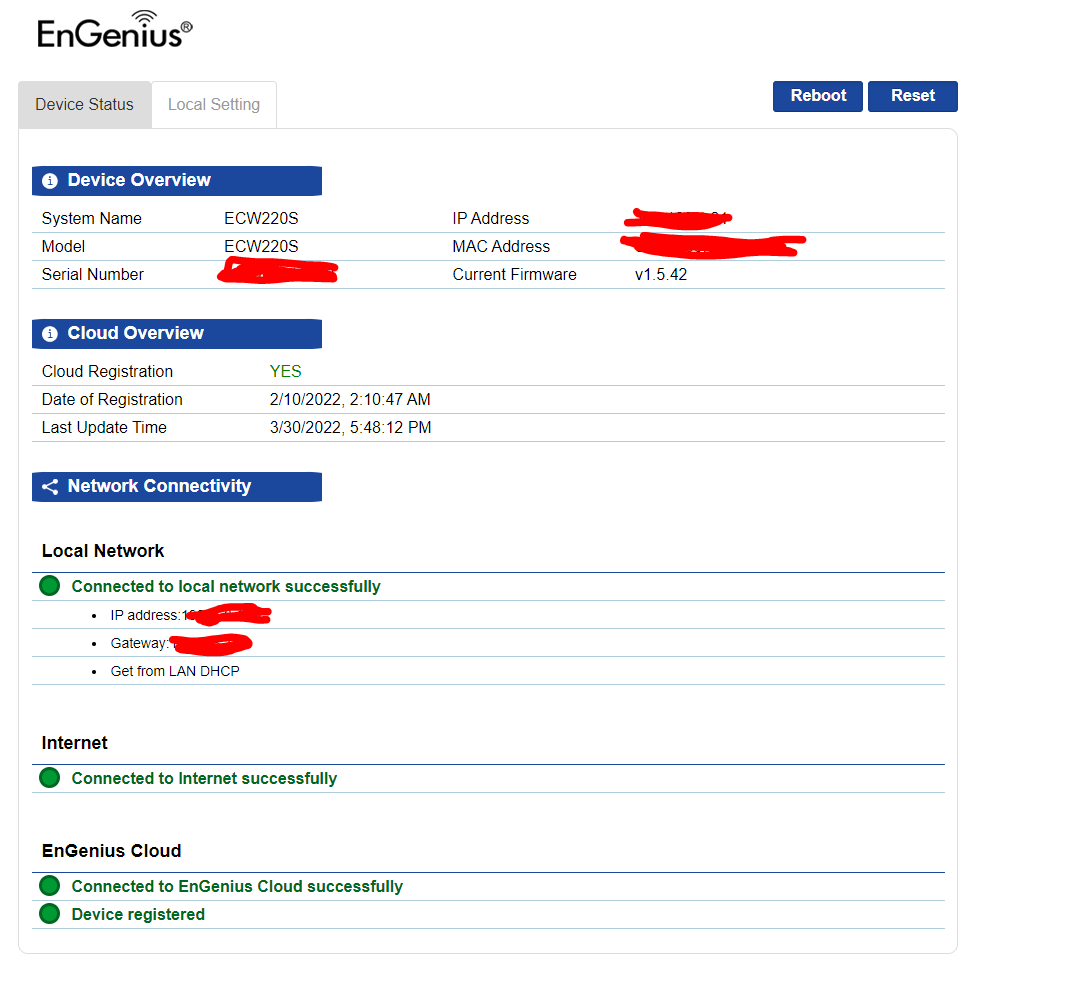
If you have seen any of our EnGenius coverage in the past, a majority of their products have now integrated their EnGenius Cloud for their software. You can log in to the ECW220S directly just like with any of their other cloud-based products but the interface is limited to being able to reboot the device, renaming it, and setting up its network settings if you prefer a static IP. You can also see its status as well.
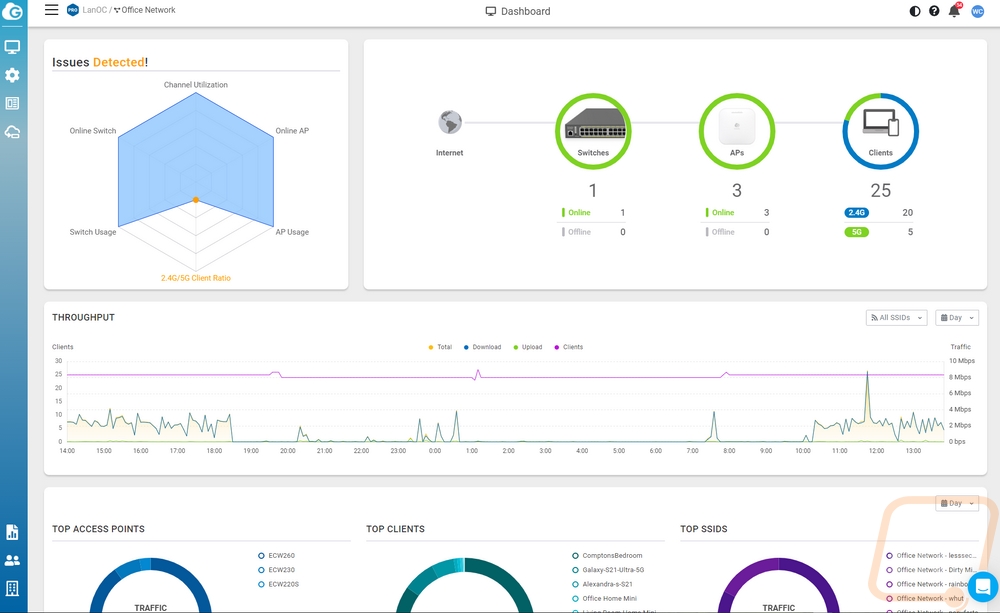
Cloud integration isn’t going to be for everyone and EnGenius does have options that skip it but none that have the security features of the ECW220S because a lot of those tie in around the cloud software itself. On the plus side of things, EnGenius Cloud makes getting things set up significantly easier. To set things up you can add the device manually on your EnGenius Cloud account through a PC or if you have the app you can scan the QR code on the back of the access point and add it to your account. Once scanned in, if you have any other access points already set up the AP will run with those settings. When you first log in with things set up this is what your landing page looks like. EnGenius has an overview to show you what devices are running and the number of clients connected at the time as well as a throughput map for the last day, breakdowns on the top access point being used, top SSIDs, and clients as well as a graph to show the overall status of your network. You can see for ours it doesn’t like that a majority of the devices connected on wireless are on 2.4GHz, but that is because a lot of smart devices can only connect at 2.4 GHz.
On the left, there are a few icons that when you mouse over them open up the menus. The top is the manage section which gets you access to the access points, switches, topology, maps and floor plans, the client list, and AirGuard. I will get into a few of those pages more in detail in a minute as they are specific to the ECW220S. The next menu is the configure menu, this is where you can dive more into settings and the two are SSID and Radio Settings, these are AP-specific pages. Cloud users lets you set up user accounts so others can access this information, this is important being an enterprise solution. You can get into firmware updates which lets you see what each device is running and pick which updates you are going to get like focusing on beta updates, stable, or even the previous stable. You can pick specific devices to test out new firmware and set up a schedule when updates should be done if there is one available. I love that they even let you know what is upcoming, mine currently says “Trial Zone devices will be upgraded to v1.5.42-1 after 4/3 (Sun). | Other devices will be upgraded to v1.5.42-1 after 4/3 (Sun).” for example. The last menu is the analyze menu which just has the event logs in it.
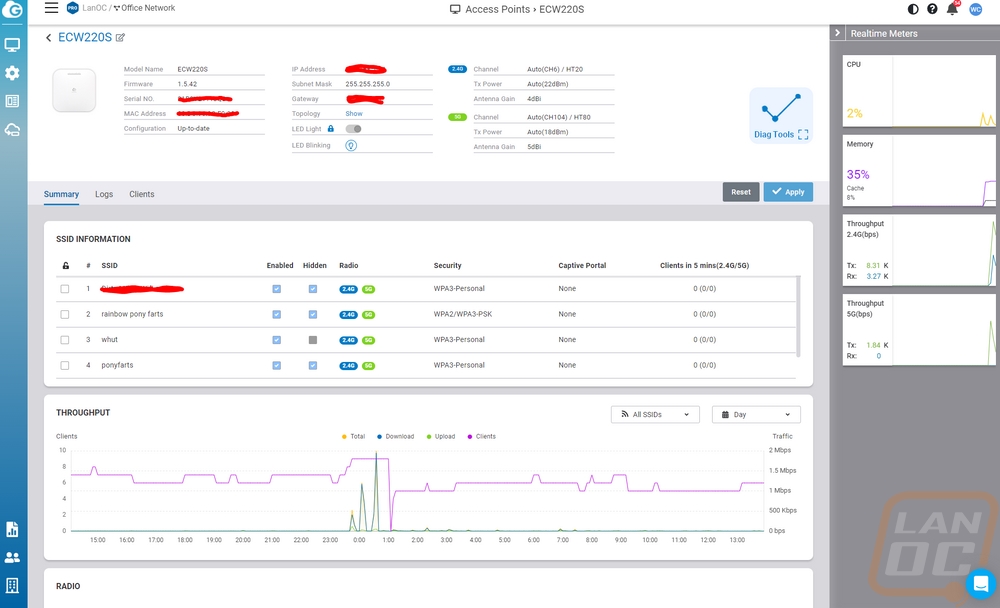
Going back to some of the menu options, the access point option in the first menu gets you a list of your access points. That page will show you what channels they are running on, their WAN and LAN IPs, firmware versions, uptime, and the number of clients. Mousing over any of them gets you options to reboot to go to the diagnostic page (which I will show in a minute), you can replace the device, or open up more details. Below is the details page for the ECW220S. Up top, they show all of the basic information like mac address, IPs, channels, channel power, and more. You can even turn on the LED light if you aren’t sure where that AP is at to help you find it. The right side of the page has meters for the CPU, memory, and throughput on both 2.4 GHz and 5 GHz. Then they have all of your SSIDs listed with information and easy access to turn them on and off or hide them as well as their security level and the number of clients. Below that are graphs for the throughput again but this one you can change to show per SSID and put the length of time you want to check out. You can get into radio settings if you want to override the settings for the entire network as well as set the static IP of the AP as well. There are tabs that let you get to the logs for this specific device as well as a list of connected clients. That list shows you their total bandwidth being used, the name, mac, IP, SSID they are connected to, a basic vendor ID from the MAC, and an antenna strength indicator which can help you pinpoint how close they are to the AP if you are trying to find the connected device.
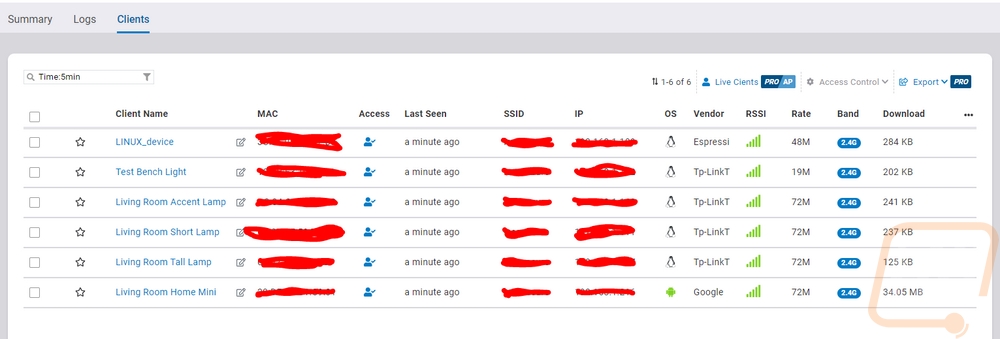
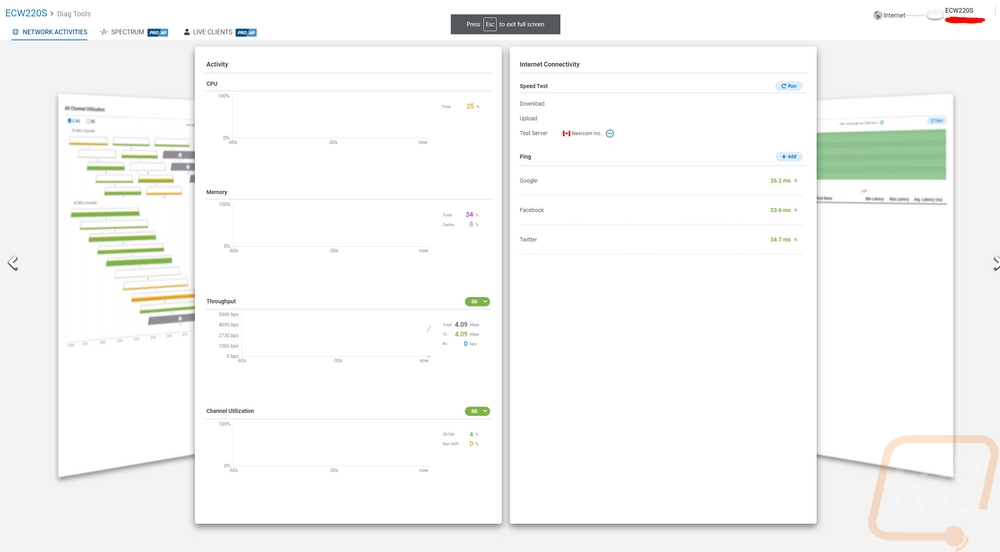
The diagnostic page opens up and is completely different than the rest of the EnGenius Cloud integrated software it also automatically full screens itself. Everything is listed on pages and you can flip through multiple pages. The first pages are simple with CPU and memory activity and things like internet connectivity which you can run speed tests and check the ping on a few default websites or add your own. The next page lets you see a traceroute in a graph form as well as has the hops listed out traditionally as well.
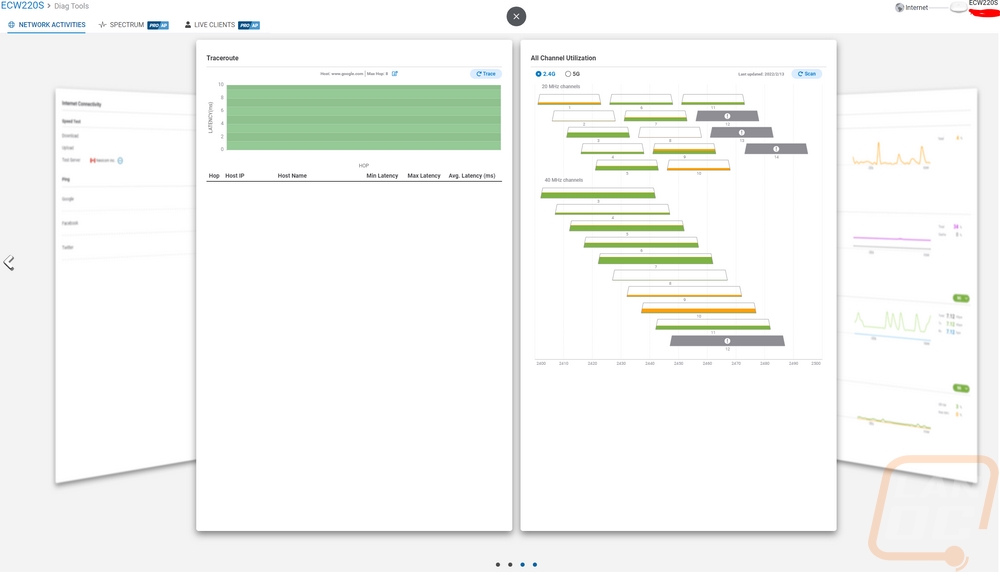
You start to get into more interesting stuff when you get into the channel utilization page which can be set to 2.4 GHz or 5 GHz. This test has to be run and while this is supported on any of the EnGenius APs the ECW220S has dedicated scanning radios so this can be run without interrupting the service but on a non-S model this would turn off the access point while running the scan. They break down all of the channels and show you how much activity is going on in that channel. A lot of people would set up their wireless to auto-select the channel, but here you can see activity and use it to force a channel if you prefer or to just get a better idea of why you are having issues.
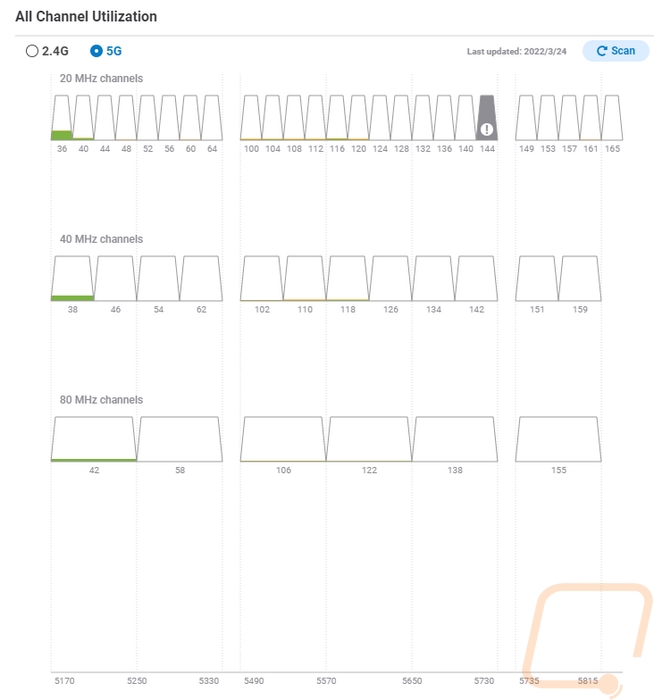
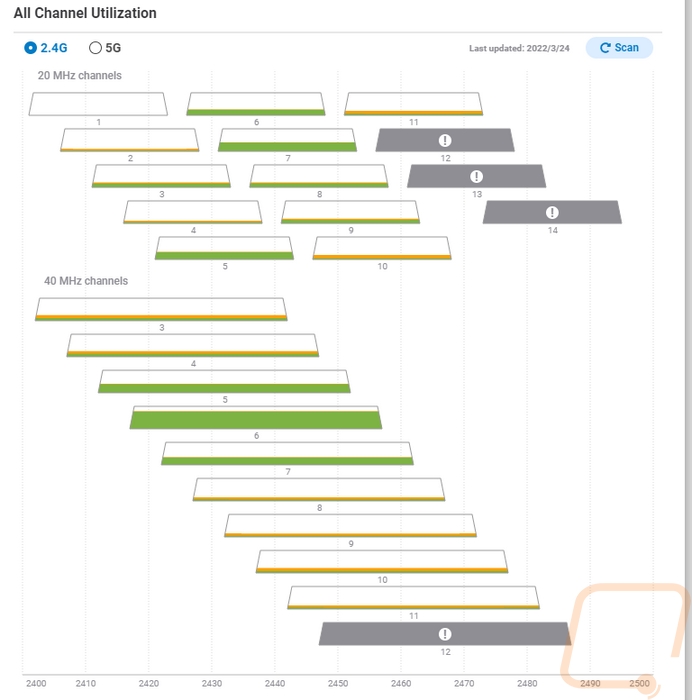
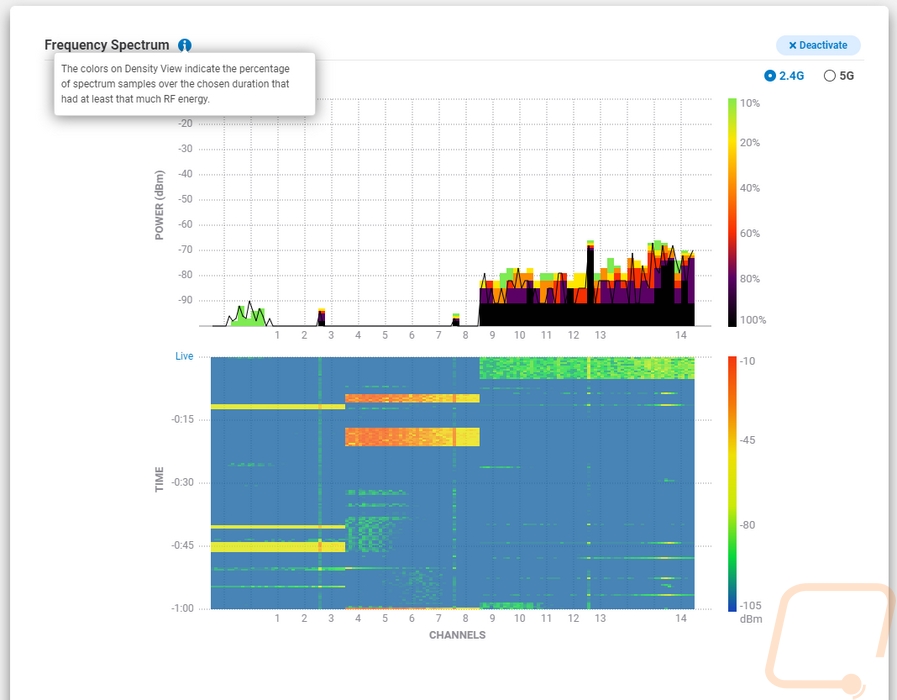
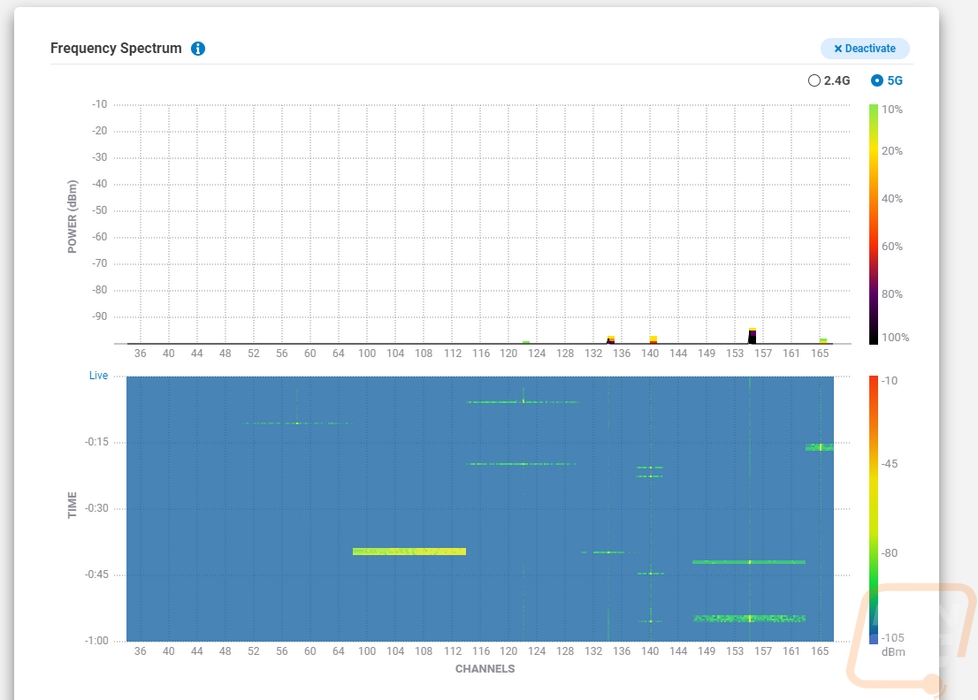
Up top there is a Spectrum tab, this is specific to the ECW220S and ECW230S and it also requires an EnGenius Cloud Pro account. The idea is similar to the channel breakdown above, but here we are using the dedicated scanning radios to graph out the activity across the channels. The top graph shows a live look at the activity and the bottom graph shows that activity over time. There are pages for 2.4 GHz and 5 GHz and only one at a time can be running. They also really show how much more 5G has for channels.
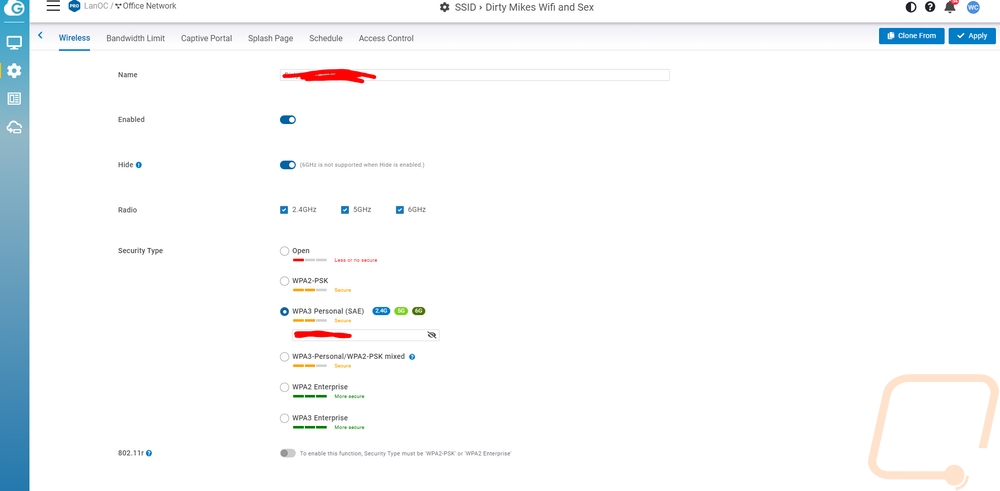
The SSID page is split off from the radio settings and this is where you would set up your wireless networks for your location. The first page is where you are setting up the name, turning it on or off, hiding it, and setting up the security which the ECW220S does let you set up WPA3 personal or enterprise, WPA2 enterprise, or PSK, or open. They also have an option that mixes WPA3 where it is supported and WPA2 PSK which is nice if this is a personal environment and you have devices that don’t support WPA3 but for that situation, I personally am running a WPA3 network for devices that support it and other devices that don’t have to be on a different SSID that is more locked down. This page when you scroll down also lets you set up specific VLANs for any device on a specific SSID. This is also where you set up how the clients will get their IPs with NAT, Bridge, or Tunnel all supported (Tunnel is only on Pro accounts). Another big setting here is the 802.11w which you should keep on, this helps prevent deauthentication attacks and dis-association attacks.
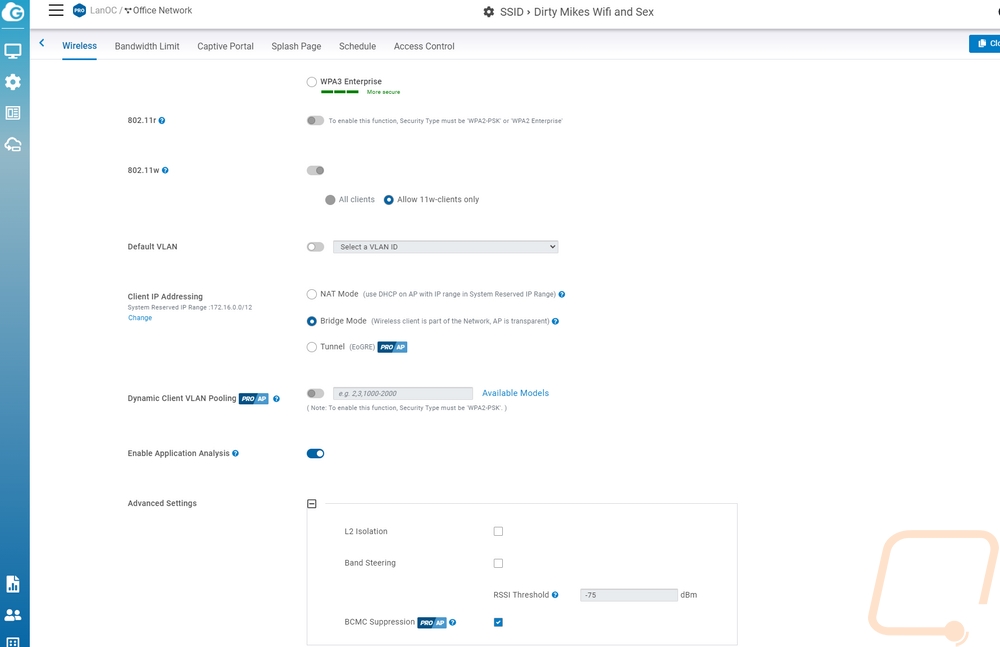
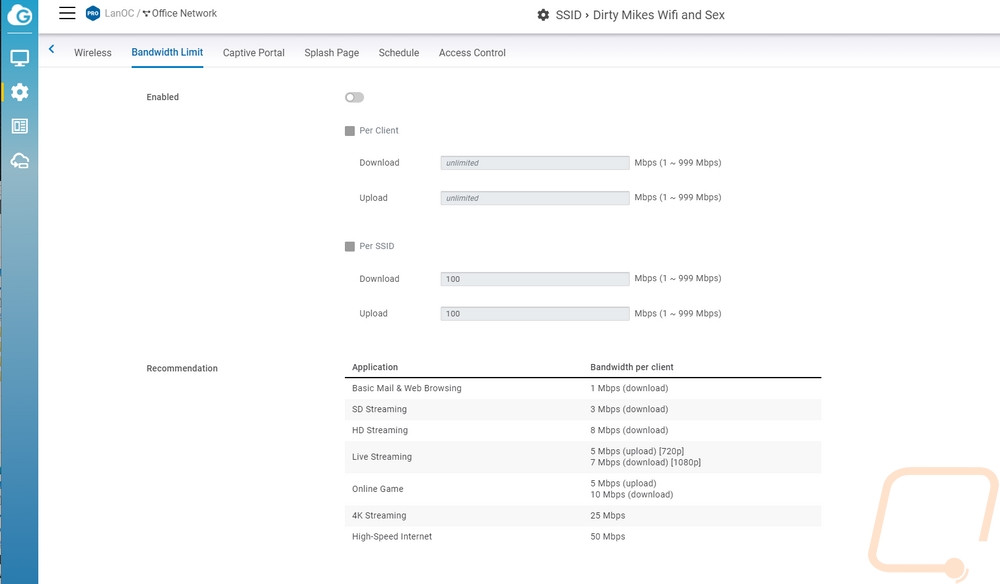
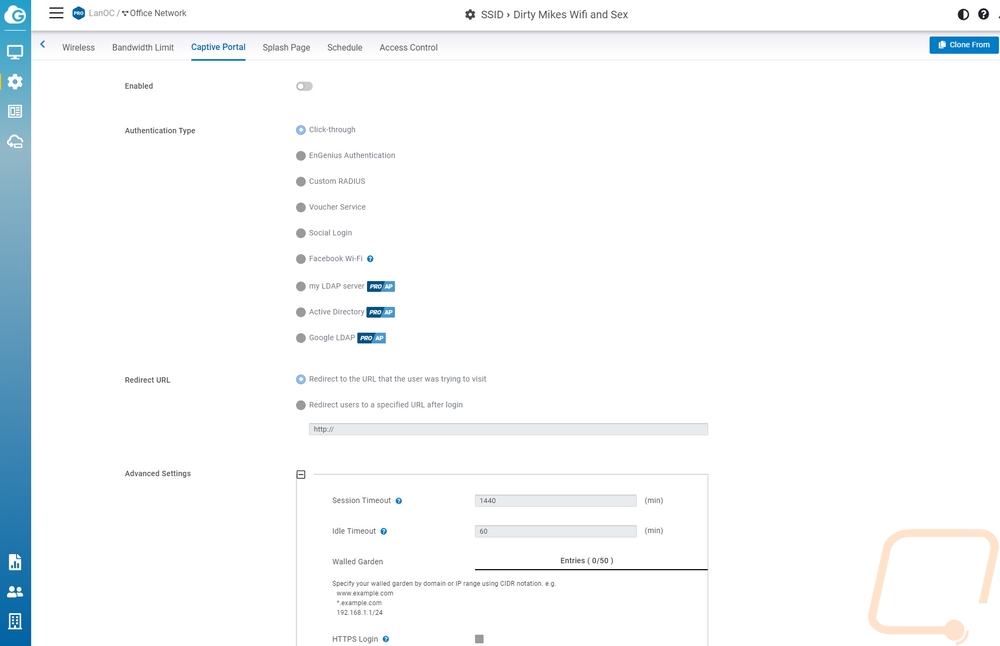
The next tab is for setting up bandwidth limits. The ECW220S is enterprise-focused and you may be setting up an open network that customers are accessing and you can set limits here per client or for an entire SSID to help prevent all of your bandwidth from being sucked down by a big update or if you have less overall bandwidth limit streaming. The tab after that is for the captive portal and if you have ever been on the wireless at a hotel, store, or eatery you have seen these. Before people access the internet you can have them sign in through a variety of methods or just click through to agree to terms. The splash page on the next tab goes with this as well which is where you set up a local or external page.
Back to controlling your wireless, there is a schedule page. I really like this one for businesses, you can turn wireless on specific SSIDs off when you aren’t open but even for home use this can be a great way to limit the internet for your kids or you could even force specific devices to only work on an SSID (like game consoles) and give them a schedule. The last page is access control and this ties in with that last suggestion. You can block or VIP devices by their mac address.
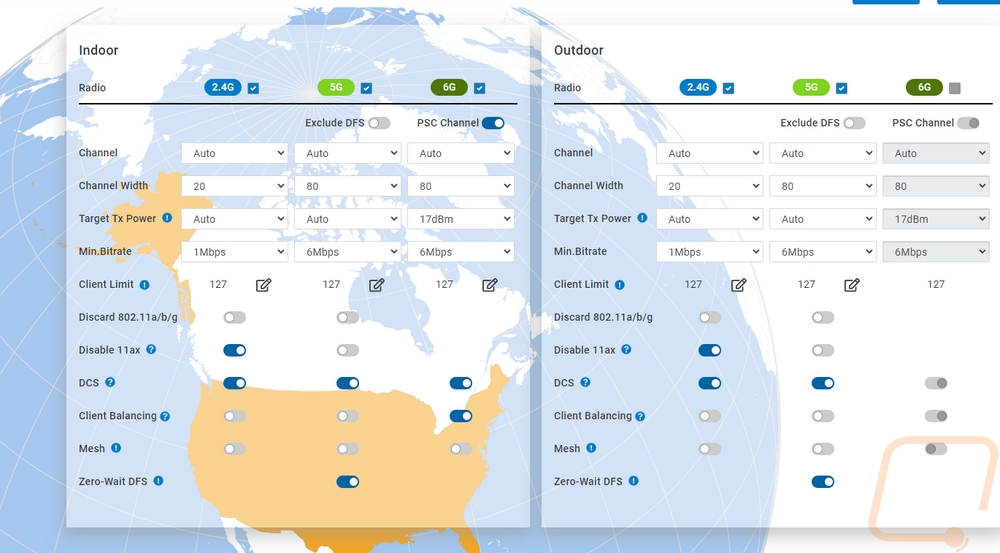
EnGenius has all of the actual radio settings on their own page. This is set up so you can configure your entire location so they have things split up between indoor and outdoor even if you are just running the ECW220S. Then from there, they have 2.4G, 5G, and 6G for each of the frequencies. The 6G setting doesn’t apply to the ECW220S as it is a WiFi 6 AP, not a WiFi 6E which adds support for the 6 GHz spectrum. This is where you can set the channel for your APs to Auto or a specific channel and get into details like the channel width, minimum bitrate, and transmitting power. EnGenius lets you set client limits for each and then they have details like turning mesh on or off. Basically, wireless mesh networking is supported, but if you are running POE to your AP then you also have networked directly at each switch and that is going to be faster. The ECW220S and ECW230S also add in the ability to have Zero-Wait DFS. Basically, with the extra radios dedicated to scanning, they can quickly spot radar interference and change channels, normally when this happens you have to wait a minute to be booted from the channel, this avoids that downtime.
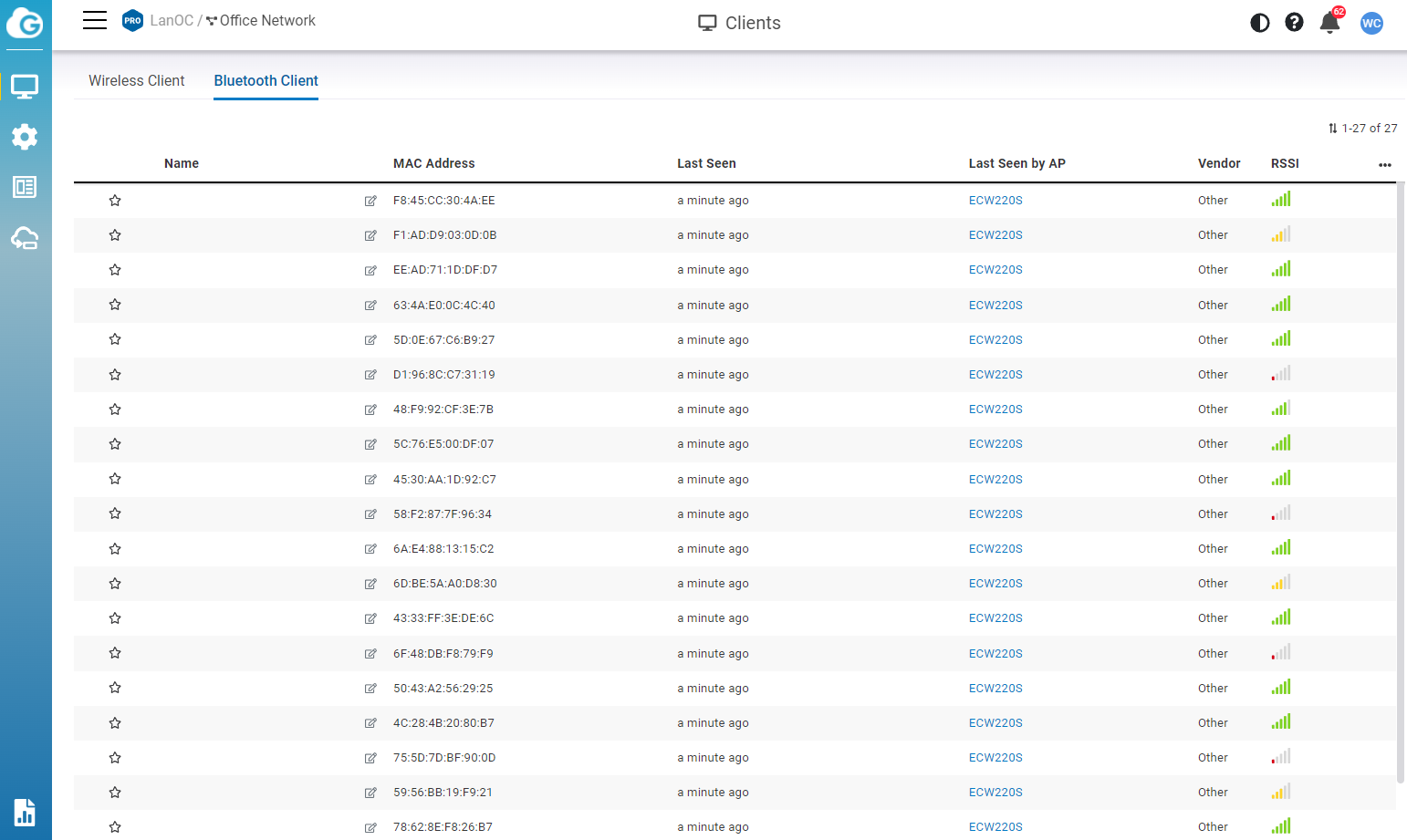
Under the client listing one of the features added to the ECW220S and ECW230S is a BLE5 or low energy Bluetooth. This scans for Bluetooth devices and will list them off. There aren’t any big interactions in the EnGenius Cloud software with this addition other than this list which does have the signal strength listed if you were trying to maybe pinpoint where a device is. But the big thing here is they can provide an API to integrate this scanning with third-party applications.
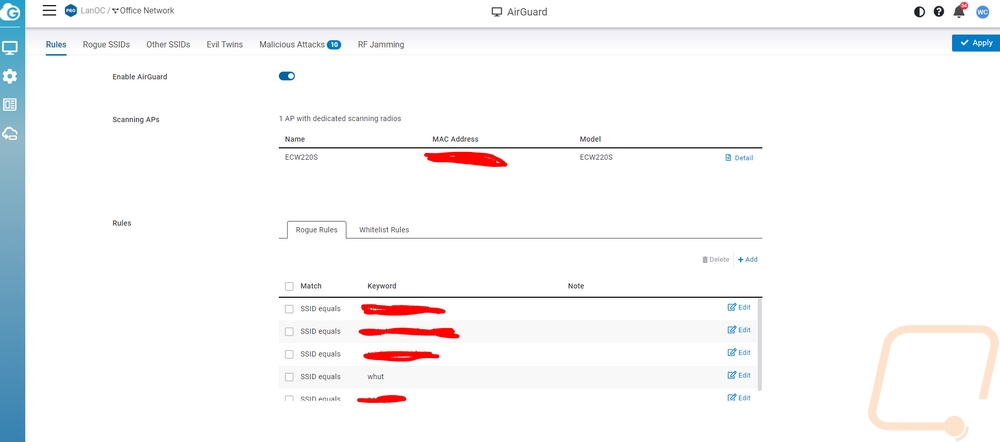
With most of the standard software features out of the way. That leaves the biggest change added to the ECW220S which is the new AirGuard page. This is where you can get in and work with AirGuard to help find and deal with security issues. EnGenius uses the two additional radios to scan around the ECW220S all of the time to look for rogue access points and other wireless threats. The AirGuard page is broken down into six different pages and the first is the rule page where you can set a few things up. For starters you need to turn AirGuard on, then below that, you can see all of the access points that support it. For our network, we have the EnGenius cloud-supported access points but only the ECW220S has the additional antennas and processing power to support this feature. Speaking of processing power, I should mention that the ECW220S has the same processor as the ECW220 but they have doubled the clock speed from 1 GHz up to 2 GHz. For the setup, you do need to add in your current wireless SSID names. When you do this you can set AirGuard to search for anything that perfectly equals your SSID or you can search for anything with the word at all. So for our network, I set up one for each of our SSIDs but I also went in and set up a few with specific words that wouldn’t be in any other network around us. A good example of this would be your business name or for personal use maybe your last name. A few of our SSIDs have very unique words in them, I also set up rules to look for those words as well. We would want to know if anyone was using an SSID around us that was even close to ours.
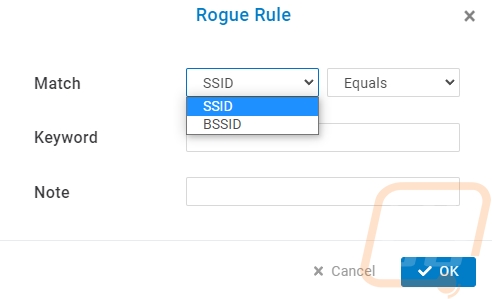
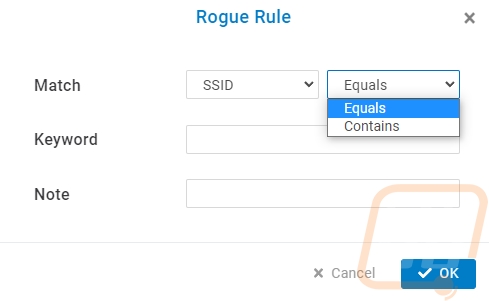
Once you have your rules set up AirGuard will be on the lookout for those. In addition to that, there are a few other things that it is always scanning for so even without your rule setup there are a few things you will see on the other tabs. The Other SSIDs page is going to start to fill up and this will depend on how many other wireless networks you have around you and the traffic around you as well. With ours, I was blown away by the number of hotspots that AirGuard picked up. But there are a lot of cars with hotspots built-in and people running them on their phones as well. The Other SSIDs page will let you know the mac address of that SSID and show how many others if multiple mac addresses are coming up. You get the manufacturer name if the mac decodes and you can see things like the channel they run on, its security type, and of course when you first saw the device and when you last saw it. You can also add a note if you happen to know anything about it, so if it is a neighboring AP you can put a note as to where it is located if you know.
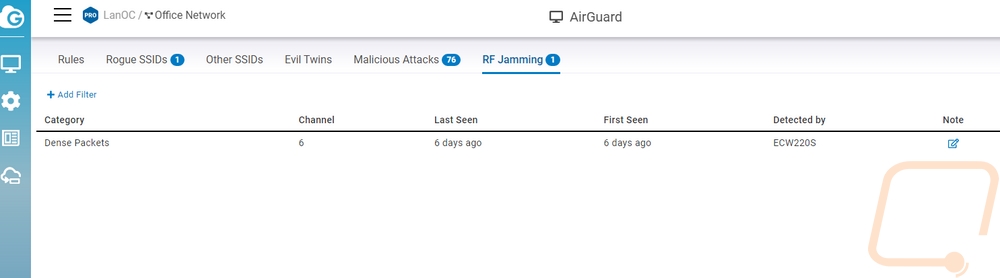
Down at the end, there is a page for RF jamming and interestingly enough when I first hooked up the ECW220S I ran into this and other issues right away. This is a picture with one event showing but at one point this page was filled up with incidents. The ECW220S which scanning looks across the entire frequency range as we saw on the diagnostic page. When you get interference spanning one or more channels it will log it here. This isn’t always malicious, it could be a microwave or something else causing problems. But with a normal network, you wouldn’t even know it was happening. You would notice that your wireless is slow, but that could be caused by multiple things. With AirGuard you can help pinpoint the issue. If you are running more than one AirGuard supported AP you can also use the detected by to narrow down where it is coming from as well.
Sadly I don’t have any examples of rogue SSIDs or evil twins. I did run into them but they drop off of the list after a week. As you can see from the pictures below, as soon as I had the ECW220S up and running I had a whole list of attacks showing up. This was a surprise, I thought for this review we might have to attack our own network but as it turned out the network was already under attack. In fact, looking at the SSIDs in the other SSID section it looked like some of the neighboring networks were under attack as well. What really gave that away was of all of the SSIDs that I already knew were nearby I was seeing some pop up that were cloning the first name or part of the name with random letters or numbers in them trying to clone them. In addition to that, we were getting the RF jamming at times and both de-authentication and dis-association attacks. Basically, there were one or more devices that were scanning the SSIDs around and then trying to clone or be similar and using attacks to kick people off their network to try to get them to connect to the rogue device.
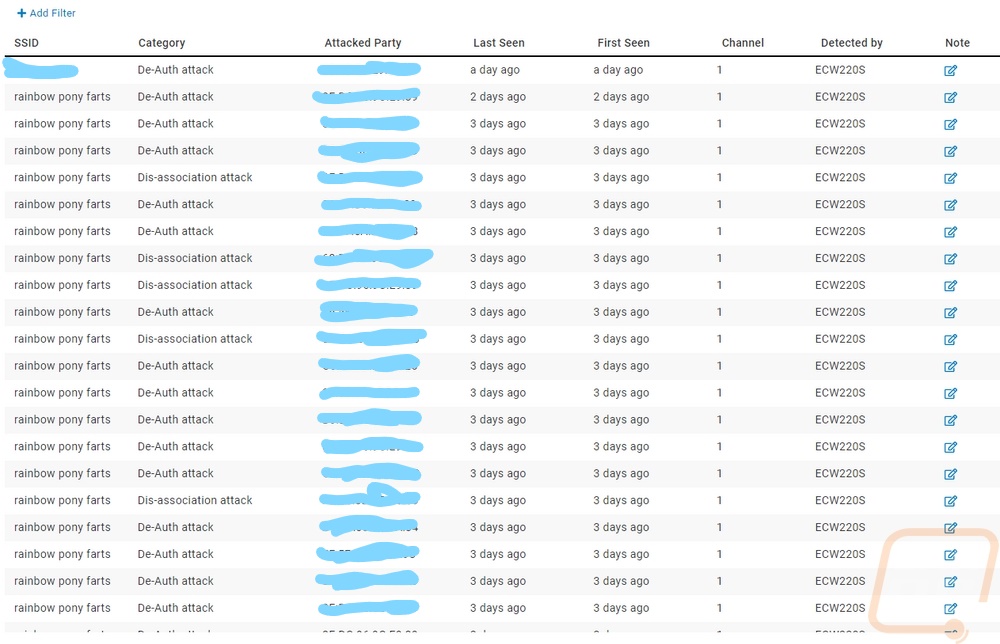
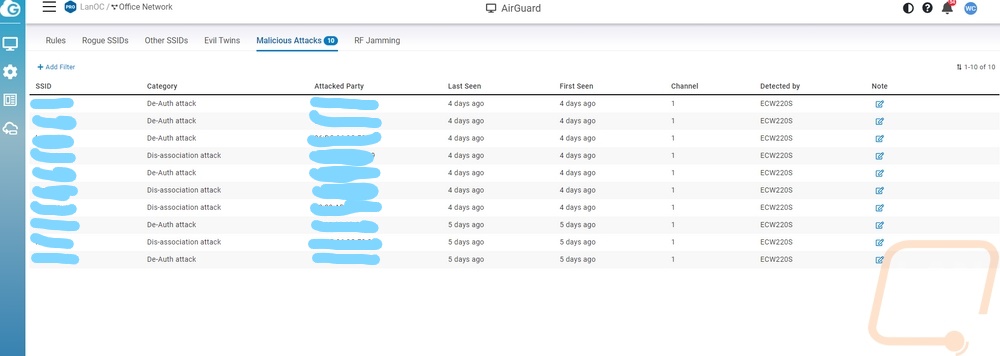
With the above issue, I decided to finally make a few changes to our wireless network that I had been putting off for years. We moved four years ago and even with the move and later changing up our network devices I kept the same SSID for part of our network. Specifically, I kept the SSID and password because we have a lot of wireless smart devices that I didn’t want to go around and reset and start over on. It would be great if some of the devices like Google Speakers would have an option to put in a new SSID but you have to hard reset them and set things up on the new SSID. I also wanted to switch over to WPA3 where possible as well. Most importantly, I also really needed to hide some of the SSIDs. It isn’t perfect, but having your SSIDs exposed makes it really easy for the rogue device or someone nearby to poke and prod at the network. So I started by setting up all new SSIDs, new passwords, and hiding them as well. I moved our most secure devices over and the attacks continued on the original SSID. From there I went through and move a few more devices at a time and kept an eye on the attacks which don’t happen all of the time. I did this over a few weeks, like I said we have a lot of devices. I had almost all of them moved over to the new SSID when I finally moved something and our hidden network started to get attacked. We have a LOT of KASA bulbs, switches, and outlets. I didn’t have any trouble with most, but as it turns out the bulbs in our front lights were causing the problems. Turning them off for a few days stopped the dis-association and de-auth attacks and I am swapping those lights out. I haven’t been able to find any information on other Kasa bulbs having this issue, but please reach out if you have seen this.